Forwarding Process
Forwarding Process
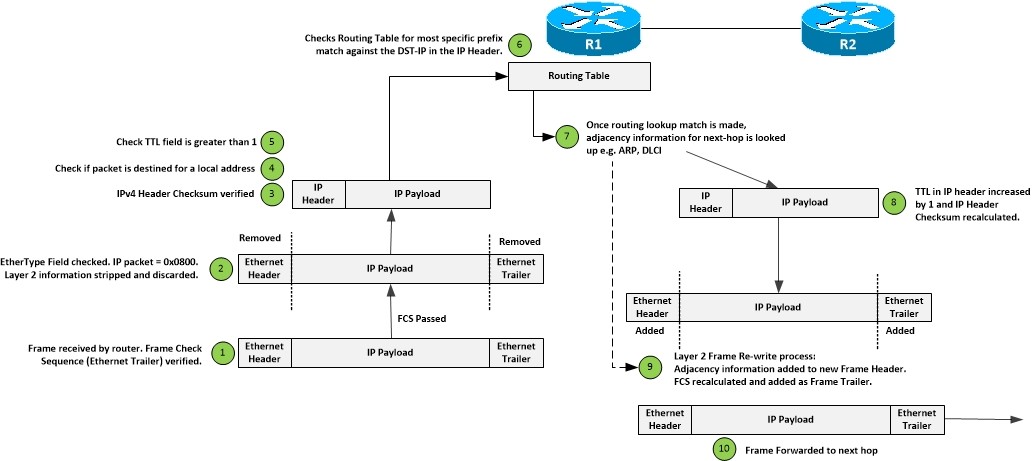
Figure 1 – Process Switching
- Key steps in the forwarding process of packets
- Router receives frame and checks Frame Check Sequence
- If there is an error, the frame is dropped. No recovery mechanism
- Router checks the EtherType field for type of packet (0x0800). Strips Layer 2 information from frame.
- IPv4 header checksum verified. IPv6 headers do not have a checksum
- If error packet is discarded
- ‘Router checks if DST-IP is one of the local interface addresses.
- If it is, Router looks at Protocol field in IP header, identifying protocol. Passes packet to upper-layer service.
- If not a local address, Router checks the TTL is more than 1
- If not, packet dropped, ICMP Time Exceeded message sent to originator
- If TTL > 1, Router checks the Routing Table for most specific prefix to match the packets DST-IP against
- Router checks the Adjacency Table to lookup the Layer 2 information for the matched prefixes next-hop.
- Router updates the IP header TTL value and recalculates the checksum
- Router encapsulates IP packet in new Layer 2 header and recalculated FCS trailer
- Frame forwarded to next-hop destination
| Switching Method |
Forwarding Information |
Load-Balancing |
| Process Switching |
Routing Table |
Per Packet |
| Fast Switching |
Route-cache (per flow) |
Per destination IP |
| CEF |
FIB and Adjacency Table |
Per hash or per packet |
Process Switching
- Legacy method of switching packets
- All packets are forwarded to the CPU to make the forwarding decision
- CPU intensive process
- Load balancing per-packet
- Follows the basic process outlined in the Forwarding Process section above
[_/su_spoiler]
Fast Switching
- Also known as route once, forward many times
- Improvement on Process Switching but still a legacy method, replaced by CEF.
- Discontinued from IOS version 12.2(25)S and 12.4(20)T onwards
- Load balancing can be performed per IP address
- First packet to a destination is Process Switched
- Router adds the lookup information to the fast-switching cache (or route-cache)
- Route-Cache contains DST-IP address, Next-hop information and Layer 2 header information that needs to be added to the packet before forwarding (covered by Step 6)
- All subsequent packets to the same destination re-use the information from the cache
- If there is no cache entry for a packet, it is process switched again
[_/su_spoiler]
Cisco Express Forwarding (CEF)
- Used as a rapid method for hardware packet switching
- De-facto standard in Cisco IP equipment
- Most intensive part of packet forwarding is constructing the Layer 2 information, also called Layer 2 frame re-writing
- Upper layer information doesn't change significantly apart from Hop Count/TTL decremented and checksum recalculated
- CEF consists of 2 parts:
- Forwarding Information Base (FIB)
- Contains all destination prefixes from RIB and egress interface
- Adjacency Table
- Uses next-hop IP's and ARP to translate into Later 2 information
- Pre-constructs Layer 2 frame header information for next-hop
- Prevents the need for individual lookups
- Once FIB and Adjacency Table are populated, the Routing Table is not used any-more where there is a FIB entry
- Routing Table only used as a source of information for the FIB and Adjacency Table
- CEF uses TCAM (Ternary Content Addressable Memory) to store FIB information which is hardware accelerated and performs very fast lookups
- Load balancing per hash of the source and destination, or per packet
- CEF is enabled by default on Cisco devices
- Can be configured manually
- IPv4 CEF can run without IPv6 CEF running but not the other way around.
- IPv6 CEF has to have IPv4 CEF enabled to work
CEF Load Balancing
- Supports 2 different methods:
- Per Packet
- Packets to a destination are load balanced across multiple paths on a per-packet basis
- Per Destination
- Default method
- Takes the source and destination, as well as other values and generates a hash
- AKA per-flow load balancing
- Different hash values are load balanced across different paths
- Same hash values follow the same path
- Creates a load-share table between the FIB and the Adjacency Table
- Contains up to 16 pointers to Adjacency Table entries
- Proportionally distributed to costs of routes to same destination
- Example:
- 2 equal cost paths to destination prefix
- 8 load-share entries will point to one next-hop adjacency
- The other 8 will point to the other adjacency
- If there are 3 equal-cost paths, only 15 entries will be populated
- Each adjacency with 5 load-share entries each
- Hash values are used as an index into the load-share table to select one of he paths to the destination
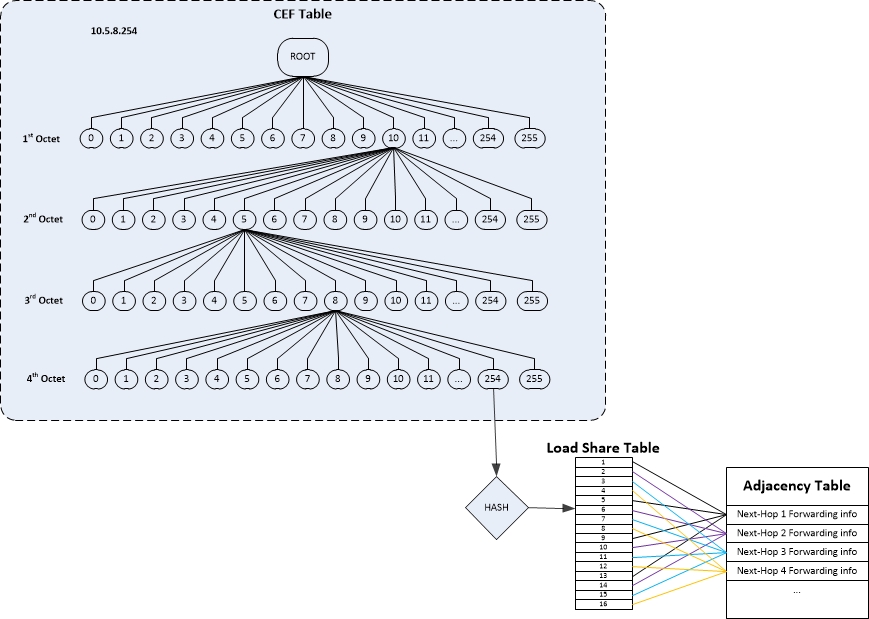
Figure 2 - CEF Table
- CEF load sharing is activated on EGRESS interfaces
- Command:
- (config-if)#ip load-share [per-destination | per-packet]
CEF Polarization

Figure 3 - CEF polarization
- Caused by all routers along the path to a specific destination using the same hashing method.
- Flows that produce the same hash in line with the cef load-balancing algorithm will follow the same path.
- This means that the next router in the path will no longer load-share the flows and all flows from that point will be sent through a single path to the destination
- To avoid CEF polarization;
- CEF implements a 4 Byte (32 bit) random number called the Unique-ID/Universal-ID.
- Randomly generated upon device boot-up
- Can be configured manually
- Command:
- (config)#ip cef load-sharing algorithm universal <ID value>
- (config)#ipv6 cef load-sharing algorithm
- Each router will then provide a unique hash value for individual traffic flows, circumventing CEF polarization
- If a router produces a specific hash value for a certain number of flows and forwards on to the next device, the next device will be able to produce a different set of hashes based on the unique-ID/universal-ID
CEF Load-Sharing
- Different load-sharing algorithms:
- Original algorithm
- Unseeded
- Prone to CEF polarization
- Universal algorithm
- Uses unique-ID/universal-ID seed to avoid CEF polarization
- Tunnel algorithm
- Builds on Universal algorithm
- Designed for network implementations where tunnels are used
- where there are fewer numbers of source/destination flows
- Avoids CEF polarization
- L4 port algorithm
- Builds on Universal algorithm
- Uses L4 information in hash calculations
- Avoids CEF polarization
- To view the current unique-ID/universal-ID and load-sharing value use the following commands:
- #show cef state
- #show ip cef summary
- #show ip cef detail
- Cisco Catalyst 6500 hashing algorithm methods:
- Default
- Uses source/destination addresses, unique-ID/universal-ID with unequal weights assigned to each link
- Avoids CEF polarization
- Simple
- Uses source/destination addresses, with equal weights assigned to each link
- Doesn't use unique-ID/universal-ID
- Prone to CEF polarization
- Full
- Uses source/destination address, source/destination L4 port
- Doesn't use unique-Id/universal-ID
- Prone to CEF polarization
- Uses unequal weights assigned to each link
- Full Simple
- Uses source/destination address, source/destination L4 port
- Doesn't use unique-Id/universal-ID
- Prone to CEF polarization
- Uses equal weights assigned to each link
- Avoids unequal traffic split like Full mode
[_/su_spoiler]
ARP
ARP
- Maps Layer 3 IP addresses to Layer 2 MAC addresses
- Default ARP timeout is 14,400 seconds (4 Hours)
- Can be configured with command:
- (config)#arp timeout <seconds>
- Can create static entries in the ARP table
- Command:
- (config)#arp <ip address> <mac address> arpa
- IPv4 packets Ethernet protocol type is 0x0800
- ARP Ethernet protocol type is 0x0806
- Proxy ARP allows routers to respond on other nodes behalf
- Useful if a default gateway or next-hop IP isn’t set
- Example would be on static routing and only setting the outgoing interface not the next-hop IP address
- Example:
- If 2 routers were connected, RouterA and RouterB and RouterA wanted to ping the loopback address of RouterB but didn’t have a next-hop IP address set, just an outgoing interface.
- RouterA would perform ARP on that address and RouterB would respond with an ARP Reply saying they host that address and to forward the frame on to them.
- Enabled by default in IOS
- The ARP message has a TARGET field of all 0’s for the MAC address, and a target IP address of the IP address whose MAC address needs to be learned
Administrative Distance
Default Administrative Distances
| Type |
AD |
| Connected |
0 |
| Static |
1 |
| EIGRP Summary Address |
5 |
| BGP External |
20 |
| EIGRP Internal |
90 |
| OSPF |
110 |
| ISIS |
115 |
| RIP |
120 |
| On-Demand Routing (ODR) |
160 |
| EIGRP External |
170 |
| BGP Internal |
200 |
| NHRP |
250 |
| Floating Static Route |
254 |
| Inaccessible |
255 |
IP Unnumbered
IP Unnumbered
- Enables IP connectivity on point-to-point (serial) interfaces
- Uses an IP address assigned to another interface
Static Routes
Static routes
- Used to identify a path to a prefix not locally connected
- Not scalable
- Administrative Distance = 1
- All static routes have a metric of 0 (not AD)
- Installs all static routes created for ECMP
- Not limited to 4 or 8 multiple paths
- Provide a next-hop based on:
- Interface
- Not recommended
- Route will exist in the routing table providing the status of the interface is up/up
- Router will perform ARP resolution for destination to all connected routers on broadcast segment
- Requires proxy-arp to be enabled on connecting router(s)
- If used by many packets to different destinations, it can cause high processor utilisation and large ARP-cache
- IP address
- Prevents the router performing ARP request on each destination
- ARP resolution only for next-hop IP address
- Next-hop address must be recursable or reachable
- If the next-hop IP interface goes down, the router could find an alternate path to the next-hop through route-recursion,
- Should use both interface and IP in this instance to force traffic a specific way
- Both Interface and IP address
- Disables ARP lookup for destination prefix
- ARP still happens for Next-Hop IP address
- Route will stay in routing table as long as interface stays in the up/up position
- Route will remote itself if the interface goes down, even if the next-hop is accessible through route-recursion
- DHCP
- Specifies the next hop is the default gateway learned through DHCP
- The prefix specified in the route can be:
- Host address
- Subnet
- Group of Subnets – Summary address
- Major network number
- Group of major network numbers (Supernet)
- Default address (0.0.0.0/0)
- The following options can be applied to static route
- Distance
- Sets the Administrative Distance preference of a static route, not metric
- Value can be 1 – 255
- Tag
- Applies a tag to the static route
- Value can be 1 – 4294967295
- Name
- Provides a descriptive name for the route to help identify it in the configuration
- Track
- Provides reliability tracking using IP SLA and Enhanced Object Tracking (EOT)
- If Tracker returns ‘OK’ message, install route in routing table
- If tracker returns ‘FAIL’ message, remove the route from the table
- Permanent
- Installs the route in the routing table even if the Next-Hop or outgoing interface aren’t up or available
- Command:
- (config)#ip route <dst prefix> <dst prefix mask> [<outgoing-interface> | <next-hop IP>] <options>
- Example:
- Install a route to 10.1.1.0/24 in the routing table permanently, with an AD of 3, and a next hop out Ethernet0/0 with IP 1.2.3.4
- (config)#ip route 10.1.1.0 255.255.255.0 Ethernet0/0 1.2.3.4 3 permanent
- Static routes can be revalidated based on time
- Default is 60 seconds
- Command:
- (config)#ip route static adjust-time <secs>
- Install routes recursive via next hop
- Feature to counter new CEF hierarchy design
- CEF changed from flat structure to hierarchical from code 12.x
- Installs child routes in RIB if the next hop is a recursive lookup
- Command:
- (config)#ip route static install-routes-recursive-via-nexthop [all | multicast | route-map | vrf]
Static Routes: Floating
Static Route: Floating
- Same principle as static routes
- Less preferred than other routes in the routing table
- Appears in the table if the more preferred route fails
- Command:
- (config)#ip route <dst prefix> <dst prefix mask> <interface | next-hop IP> <AD>
- Example:
- Create a backup static route to 10.1.1.0/24 with 5.5.5.5 as next hop
- (config)#ip route 10.1.1.0 255.255.255.0 1.2.3.4 – Primary route
- (config)#ip route 10.1.1.0 255.255.255.0 5.5.5.5 20 – Backup route
Static Routes: VRF Aware
Static Routing: VRF Aware
- Assigns a static route to a specific VRF rather than the global routing table
- See VRF Lite page for more information
- Same principle and options as normal static routes
- Added vrf keyword in command
- Command:
- (config)#ip route vrf <vrf name> <dst prefix> <dst prefix mask> [<outgoing-interface> | <next-hop IP>] < options>
- Example:
- Add a static route to 10.1.1.0/24 to the VRF CUSTOMER1 with next hop of 1.2.3.4
- (config)#ip route vrf CUSTOMER1 10.1.1.0 255.255.255.0 1.2.3.4
Longest Match Routing
Longest Match Routing
- Applies the principle of “Use the longest prefix match to destination in the routing table
- Can be used for redundancy or traffic engineering
- Example:
- A router has 3 matches to the prefix 10.1.1.1 in its routing table:
- One prefix match is the default route: 0.0.0.0/0
- Another prefix match is a summary route of 10.1.0.0/16
- The last is the exact match of 10.1.1.1/32
- If all 3 of these are in the routing table at the same time, the longest match (10.1.1.1/32) will be preferred)
- Requires IP Classless to be enabled
- Enabled by default on IOS v11.3 and later
- Without IP Classless, prefix matching will only be done on classful network boundaries
- Will not forward packets to ‘supernets’
- Command:
- (config)#ip classless
Bidirectional Forwarding Detection
Bidirectional Forwarding Detection
- Open Standard RFC 5880
- Used as a keepalive between 2 peers for path failure detection
- Provides rapid neighbor failure detection
- Converges at sub-second rates
- Performed in hardware
- Avoids having to change protocol timers which are completed in CPU
- BFD is CEF switched in hardware
- Supports authentication
- MD5 with key chains
- SHA-1 with key chains
- Meticulous MD5 and SHA
- increases packet sequence number to ensure no injected / spoofed packets
- Traffic sent over port UDP/3784
- BFD control packets unicast to peer address
- Echo packet source and destination is IP address of local interface
- BFD disables ICMP redirects automatically
- Rapidly detect a neighbor adjacency or forwarding failure rather than waiting for process timers to expire
- Multiple protocols (BFD Client) register against a single BFD interface configuration
- Protocol and media independant
- Supported by following protocols
- BGP
- OSPF
- EIGRP
- IS-IS
- MPLS TE
- RIP
- FHRP
- Static Routing
- Cisco uses a single BFD instance on an interface for multiple routing protocols on the same node and will share session information between them
- BFD Version numbers:
- Cisco IOS version 12.4(9)T supports BFD version 0 and 1
- All BFD sessions come up as version 1 by default but are interoperable with version 0
- BFD sessions negotiate at the highest common version across peers
- Can be deployed on asynchronous links using ‘Echo-Mode’
- BFD can support multihop
- Catalyst BFD Multihop for SVI interfaces
- Required for BGP multihop and recursive static routes
- Does not use echo mode
- Requires the use of templates to work
- BFD supports template configurations for all BFD sessions
- (config)#bfd-template [single-hop | multi-hop] <template-name>
- BFD control parameter negotiation timer
Pre-requisites
- IP Routing needs to be enabled on all participating nodes
- CEF needs to be enabled
- BFD must be enabled on both adjacent routers
[_/su_spoiler]
Echo Mode
- Enabled by default for single-hop sessions
- Only if enabled at interface level
- If enabled at template level, requires being manually enabled within template
- Unicast packet with IP Source and Destination set to initiating BFD client
- MAC destination set to adjacent peer
- Will receive packet and send straight back to source
- Does not work for multi hop sessions
- Pre-requisites:
- BFD must be running on all participating routers
- ICMP Redirects must be disabled from the interface(s) running BFD (avoids high CPU)
- Only supported in BFD Version 1
- BFD Asynchronous mode
- Echo packets sent to the other peer and return along the same path to perform detection
- BFD session at the other end doesn't take part in forwarding the echo packets
- Reduces overall number of packets sent by BFD session between 2 neighbors
- BFD Non-Asynchronous mode (On-Demand)
- When both of the BFD peers in the session are running Echo mode
- To disable BFD Echo-Mode
- Command
- BFD packets are processed switched in non-echo mode
- Controlled using slow-timers
- Default is 1000ms (1 second)
- Command:
- (config)#bfd slow-timer <milliseconds>
[_/su_spoiler]
Adjacency Process
- Routing process starts on the router
- Required as BFD is unicast, neighbors need to be established to determine who BFD needs to peer with
- When a neighbor adjacency is formed, the routing process sends a message to the BFD process to start a BFD session
- Parameters are negotiated - Timers, Authentication, Echo mode, Version
- BFD session is established, and BFD peers begin to send control packets
[_/su_spoiler]
Failure Process
- BFD neighbor relationship is torn down due to a link failure
- BFD notifies the routing process that the neighbor is no longer available
- Routing protocol immediately tears down the adjacency
- Routing protocol will re-converge around this failure
[_/su_spoiler]
Configuration and Commands
BFD Configuration Process
- Enable / Configure BFD at the interface level for singe-hop sessions
- Command:
- (config-if)#bfd interval <local hello (milliseconds)> min-rx <remote hello (milliseconds)> multiplier <hold-time (milliseconds)>
- Timers are locally significant
- Enable routing process
- Configure BFD at the routing process level (BFD client)
-
- BGP Client:
- (config-router)#neighbor <neighbor> fall-over bfd - Enables on individual neighbors
- EIGRP Client:
- (config-router)#bfd all-interfaces - Enables on all interfaces by default
- (config-router)#bfd interface <IF> - Enables on individual interfaces
- OSPF Client:
- (config-router)#bfd all-interfaces - Enables on all interfaces by default
- (config-if)#ip ospf bfd [disable] - Enables or disables on individual interfaces
- IS-IS Client:
- (config-router)#bfd all-interfaces - Enables on all interfaces by default
- (config-router)#bfd interface <IF> - Enables or disables on individual interfaces
- (config-if)#isis bfd [disable] - Enables or disables on individual interfaces
- HSRP Client:
- (config)#standby bfd all-interfaces - Enables on all interfaces by default
- (config-if)#standby bfd - Enables or disables on individual interfaces
- Static Routing Client:
- (config)#ip route static bfd <IF> <next-hop IP> - Enables on specific interface for specific next-hop neighbor
- (config)#ip route static bfd <IF> <next-hop IP> unassociate - Starts BFD without being associated to static route, or requiring static route to be present
- (config)#ip route static bfd <destination-bfd-address> <source-bfd-address> - Enables BFD multi-hop
- (config)#bfd map [ipv4 | ipv6] <destination-prefix/len> <source-prefix/len> <bfd-template-name> - Maps multi-hop BFD session
[_/su_spoiler]
Troubleshooting Commands
- #show bfd neighbors [detail] - Displays BFD session information and adjacencies
- #debug bfd [packet | event] - Enabled BFD debugging - only shows details if there are issues with BFD
- #show ip static route - shows which static routes have BFD enabled on (indicated by a 'B')
[_/su_spoiler]
IP Event Dampening
IP Event Dampening
- Allows suppression of flapping interfaces
- Has to be applied to physical interfaces
- Router assigns to each interface a dynamic figure that reflects the interfaces stability
- When an interface flaps it is assigned a penalty
- Default 1000 per flap
- The more it flaps, the more penalties it accumulates
- There is a time period called HALF_LIFE
- The penalty is decreased at a rate that reduces it to half the original value at the end of each HALF_LIFE
- Eventually reduces to 0
- Penalties can be cleared manually
- If the penalty exceeds the SUPPRESS LIMIT the prefix associated with the interface is suppressed/damped or no longer advertised
- The prefix of the interface is dampened until the HALF_LIFE reduces the penalty to below the REUSE LIMIT
- Default REUSE LIMIT is 1000
- Checked every 10 seconds
- Interface prefix is then advertised again in the local RIB
- Interface prefix can not be suppressed longer than the MAXIMUM SUPPRESS LIMIT
- Normally 4 times the HALF_LIFE
- 20 minutes is default (HALF_LIFE=5 mins)
- This ensures the interface prefix that continues to get penalties for flaps isn’t permanently suppressed
- Command:
- (config-if)#dampening <HALF_LIFE> <REUSELIMIT> <SUPPRESSLIMIT> <MAXIMUMSUPPRESSTIME>
- Default Configuration:
- (config-if)#dampening 5 1000 2000 20
- #show interface dampening






