[_/su_spoiler] [_/su_spoiler] [_/su_spoiler] [_/su_spoiler] [_/su_spoiler] [_/su_spoiler] [___/su_spoiler] [___/su_spoiler] [___/su_spoiler] [__/su_spoiler] [__/su_spoiler] [__/su_spoiler] [__/su_spoiler] [_/su_spoiler] [_/su_spoiler] [_/su_spoiler] [_/su_spoiler] [_/su_spoiler] [_/su_spoiler] RIPv2 Overview Summary
Function/Feature
Description
Protocol Type
Distance Vector
RFC / Proprietary
RFC 2453
Administrative Distance (AD)
120
Algorithm
Bellman-Ford
Transport protocol
UDP port 520
Metric
Hop count – 15 is max usable metric (16 is inaccessible)
Best path selection
Lowest metric (hop count)
Hello interval
No Hello’s
Doesn’t create active neighbor adjacencies
No fault detection on neighbors
Update destination
224.0.0.9 multicast for RIPv2
Update interval
30 seconds
Full of partial updates
Full updates each update interval
On-Demand circuits send full update once, then remains silent until change occurs
Triggered updates
Yes when route changes
Authentication
Clear-text or MD5
Route-tags
On redistribution into RIP
Next-Hop field
Supports assignment of next-hop IP address for a prefix, allows an advertising router to set a different next-hop IP
RIPv2 Process
Updates
Methods of Updating
RIP Version
Metric
Authentication
RIPv2 NLRI Manipluation
Summarization
Default routing
Filtering: Distribute Lists
Standard ACLs
Extended ACLs
Prefix Lists
Filtering: Offset Lists
Filtering: Administrative Distance
Filtering: Passive Interface
Timers
Split Horizon
Split-Horizon with Poison Reverse
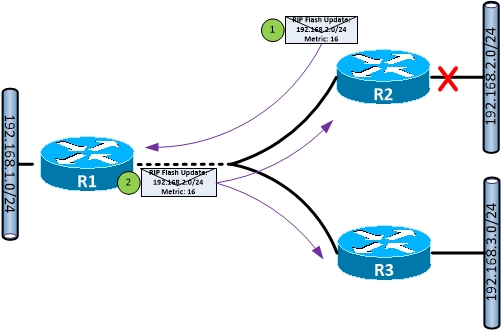
Route Poisoning
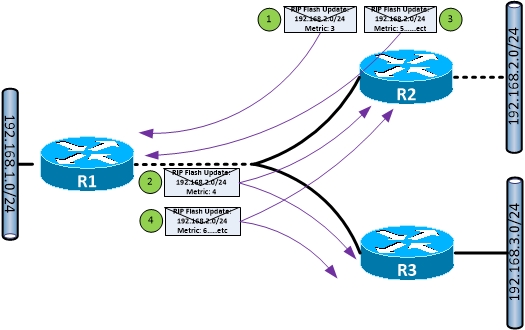
Count to Infinity
Troubleshooting Commands
RIPv2 Topic Notes