Network Address Translation Overview
Network Address Translation Overview
- Defined in RFC 1631
- Allows a host with a non-registered IP address to communicate with the Internet
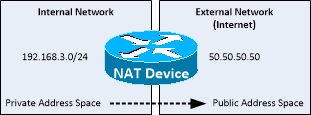
- Translates source IP, destination IP or both to allow communication with External networks
- Interfaces need to be defined if they are INSIDE or OUTSIDE the Enterprise network
- Command:
- (config-if)#ip nat inside
- (config-if)#ip nat outside
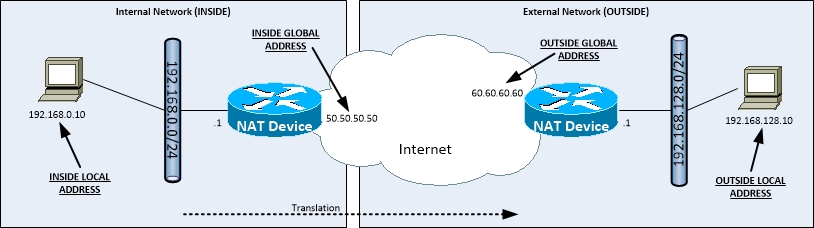
NAT Address Terminology
NAT Address Terminology
- 4 different types of NAT address types
- INSIDE LOCAL
- Address belongs to the local Enterprise network
- Represents the Private address of the host
- INSIDE GLOBAL
- Address belongs to the local Enterprise network
- Represents the Public address of the host
- Translated address
- OUTSIDE LOCAL
- Address doesn’t belong to the local Enterprise network
- Represents the Private address of the host
- Not normally seen
- OUTSIDE GLOBAL
- Address doesn’t belong to the local Enterprise network
- Represents the Public address of the host
- 2 different address zones
- INSIDE
- Addresses internal to the Enterprise network
- OUTSIDE
- Addresses external to the Enterprise network
NAT Types
NAT Types
Static NAT without PAT
- Provides a 1-to-1 mapping
- LOCAL addresses to GLOBAL addresses
- GLOBAL addresses to LOCAL addresses
- Always uses same address mapping
- Makes INSIDE LOCAL addresses available to OUTSIDE GLOBAL networks
- Command:
- (config)#ip nat inside source static <INSIDE LOCAL IP> <INSIDE GLOBAL IP>
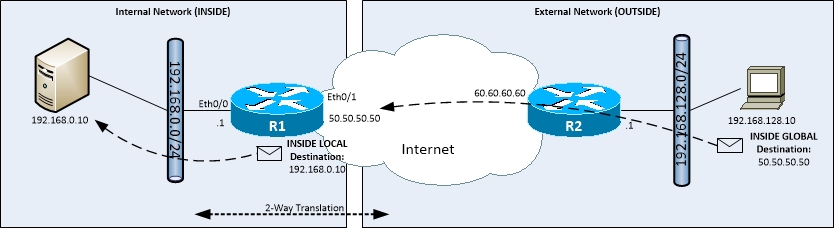
- Example:
- Client on the OUTSIDE requires access to a server on the INSIDE.
- Configuration:
- (config)#interface eth 0/0
- (config-if)#ip nat inside
- (config)#interface eth 0/1
- (config-if)#ip nat outside
- (config)#ip nat inside source static 192.168.0.10 50.50.50.50
[_/su_spoiler]
Static NAT with PAT
- Provides the same configuration as Static NAT, but can be configured based on port number
- Provides a LOCAL Port to GLOBAL Port mapping
- Command:
- (config)#ip nat inside source static [tcp | udp] <INSIDE LOCAL> <LOCAL PORT> <INSIDE GLOBAL> <GLOBAL PORT>
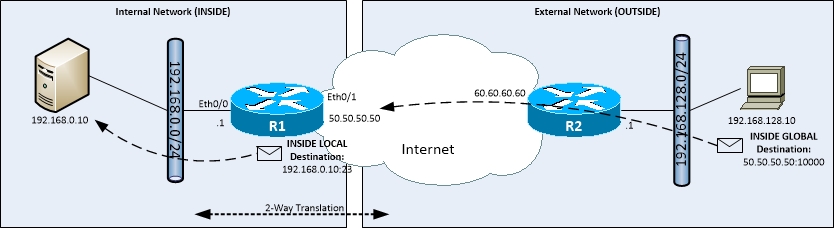
- Example:
- Client on OUTISDE requires access for telnet to INSIDE server on GLOBAL port of 10000
- Configuration:
- (config)#interface eth 0/0
- (config-if)#ip nat inside
- (config)#interface eth 0/1
- (config-if)#ip nat outside
- (config)#ip nat inside source static tcp 192.168.0.10 23 50.50.50.50 10000
[_/su_spoiler]
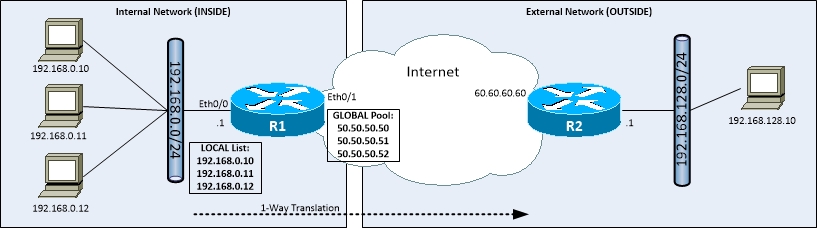
Dynamic NAT
- Provides a many-to-many mapping
- INSIDE LOCAL addresses to INSIDE GLOBAL addresses
- Uses pools of addresses
- Different LOCAL hosts can use different GLOBAL addresses from the pool
- Uses ACLs and pools to define addresses
- Commands:
- (config)#ip nat pool <pool name> <start address> <end address> netmask <subnet mask>
- (config)#ip nat inside source list <ACL of hosts to translate> pool <pool name>
[_/su_spoiler]
Dynamic NAT with PAT
- Provides a many-to-1 mapping
- INSIDE LOCAL addresses to a single INSIDE GLOBAL address
- Uses different TCP/UDP port numbers to separate translations
- Uses ACL list of addresses to translate
- Translation can use a pool of addresses or interface address
- Commands:
- (config)#ip nat pool <pool name> <start address> <end address> netmask <subnet mask>
- (config)#ip nat inside source list <ACL of hosts to translate> pool <pool name> overload
- (config)#ip nat inside source list <ACL of hosts to translate> pool interface <IF> overload

[_/su_spoiler]
Policy Dynamic NAT
[_/su_spoiler]
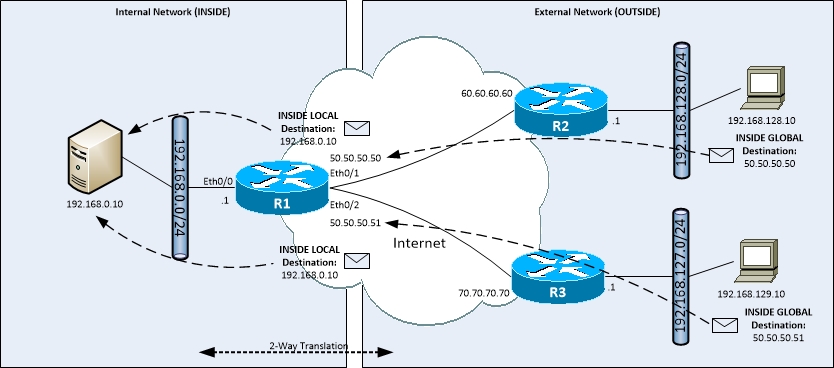
Policy Static NAT
- Combines the use of Static NAT with route maps
- Can map different INSIDE GLOBAL IP addresses to the same INSIDE LOCAL IP address
- Can be based off incoming interface
- Command:
- (config)# ip nat inside source static <INSIDE LOCAL IP> <INSIDE GLOBAL IP> route-map <route-map-name>
- Example:
- Clients from 2 different networks require access to the same INSIDE LOCAL server using different INSIDE GLOBAL addresses
- Configuration (R1):
- (config)#route-map FROM_ETH01 permit 10
- (config-route-map)#match interface Eth 0/1
- (config)#route-map FROM_ETH02 permit 10
- (config-route-map)#match interface Eth 0/2
- (config)#interface eth0/1
- (config-if)#ip nat outside
- (config)#interface eth0/2
- (config-if)#ip nat outside
- (config)#interface eth0/0
- (config-if)#ip nat inside
- (config)#ip nat inside source static 192.168.0.10 50.50.50.50 route-map FROM_ETH01
- (config)#ip nat inside source static 192.168.0.10 50.50.50.51 route-map FROM_ETH02
[_/su_spoiler]
NAT IP Aliasing
- NAT typically installs a local IP alias entry when creating a NAT rule
- This allows the router to respond to ARP requests and terminate the connection
- This can be disabled when creating a NAT rule to prevent a connection terminating on the device however still responding to ARP requests
- Commands:
- Static NAT
- (config)#ip nat inside source static <INSIDE LOCAL IP> <INSIDE GLOBAL IP> no-alias
- Static NAT with PAT
- (config)#ip nat inside source static tcp <INSIDE LOCAL IP> <INSIDE LOCAL PORT> <INSIDE GLOBAL IP> <INSIDE GLOBAL PORT> no-alais
- Example:
- Use Static NAT with PAT to translate telnet sessions from 50.50.50.50 port 1111 to 192.168.0.10 port 23 but prevent ping responding
- Command:
- (config)#ip nat inside source static tcp 192.168.0.10 23 50.50.50.50 1111 no-alias
[_/su_spoiler]
NAT Route-Maps
NAT Route-Maps
- Route-maps mean no longer need to use ACLs to match traffic
- Can match on any number of normal route-map functions
- ACLs
- Next-hop IP address
- Output interface
- Can be used with Static translations for NAT multihoming
- When static NAT and dynamic NAT are configured with the same route-map, static NAT is given preference
- Using route-maps for address translation provides the option of using IPSec with NAT
- Translation decisions can be made on destination IP address when using static entries
- Command:
- (config)# ip nat inside source route-map <route-map-name> pool <pool-name>
- Example:
- Match all traffic from the host 192.168.0.10 going out interface Ethernet 0/0 and translate the address to 50.50.50.50
- Configuration:
- (config)#access-list 1 permit host 192.168.0.10
- (config)#route-map NAT_ROUTE_MAP permit 10
- (config-route-map)#match interface Ethernet0/0
- (config-route-map)#match ip address 1
- (config)#ip nat pool NAT_POOL 50.50.50.50 50.50.50.50 prefix-length 24
- (config)#ip nat inside source route-map NAT_ROUTE_MAP pool NAT_POOL
NAT Reversible
- Used with NAT route-maps
- Route-maps create a dynamic inside to outside translation
- Doesn't allow outside hosts to initiate a connection to the inside
- Using the reversible keyword creates a static reversed NAT entry
- Can be used by outside hosts to initiate a connection from the outside to the inside
- Only allows hosts specified in the route-map to make the connection from the outside to inside
- Example:
- Match all traffic from the host 192.168.0.10 going out interface Ethernet 0/0 and translate the address to 50.50.50.50. Once the dynamic inside to outside entry is created, allow hosts on the outside to initiate connections back to hosts on the inside
- Configuration:
- (config)#access-list 1 permit host 192.168.0.10
- (config)#route-map NAT_ROUTE_MAP permit 10
- (config-route-map)#match interface Ethernet0/0
- (config-route-map)#match ip address 1
- (config)#ip nat pool NAT_POOL 50.50.50.50 50.50.50.50 prefix-length 24
- (config)#ip nat inside source route-map NAT_ROUTE_MAP pool NAT_POOL reversible
[_/su_spoiler]
NAT Virtual Interface
NAT Virtual Interface
- Removes the need for specifying NAT Inside and Outside interfaces
- Interface configured to use NAT or not use NAT.
- Enabled at interface level
- Designed for VRF traffic
- From one VRF to another VRF
- Not supported for NAT-on-a-stick
- Command:
- (config-if)#ip nat enable
- Dynamic NAT/PAT
- Command:
- (config)#ip nat inside source list <acl> pool <pool name> vrf <vrf name>
- (config)#ip nat inside source list <acl> pool <pool name> overload
- Static NAT
- Command:
- (config)#ip nat inside source static <INSIDE LOCAL IP> <INSIDE GLOBAL IP> vrf <vrf name>
NAT Static Extendable
NAT Static Extendable
- Traditionally with Static NAT provides a 1-to-1 mapping
- Static Extendable allows you to map multiple INSIDE GLOBAL addresses to the same INSIDE LOCAL address
- Command:
- (config)#ip nat inside source static <INSIDE LOCAL IP> <INSIDE GLOBAL IP> extendable
NAT Load-balancing
NAT Load-balancing
- NAT can be used to provide a basic level of load-balancing
- Also known as IOS Server Load Balancing
- Doesn’t communicate with upper layer services
- If the service is down or fails, NAT still translates address to destination
- Uses the Rotary function on pool of addresses
- REQUIRES USE OF IP ALIAS command to host the INSIDE GLOBAL IP address
- Command:
- (config)#ip nat pool <pool-name> <start-host-ip> <end-host-ip> prefix-length <prefix> type rotary
- (config)#ip nat inside destination list <outside address acl> pool <pool-name>
- (config)#ip alias <INSIDE GLOBAL IP> <port>

NAT Order of Operations
NAT Order of Operations
- Inside to Outside
- Routing first
- NAT inside to outside
- Outside to Inside
- NAT outside to inside
- Routing
Troubleshooting Commands
Troubleshooting Commands
- #show ip nat translations – Displays all NAT translations currently being done
- #show ip nat statistics – Displays NAT statistics including number of translations and expired
- #debug ip nat <acl>
- #show ip alias – Displays all IP addresses that node is hosting











